Rail Fence Cipher

Introduction
The rail fence cipher is a form of transposition cipher. Rail fence cipher is also called as Zig-Zag cipher. It derives its name from the way in which it is encoded.
Example:
Encryption
Input : "attack at once"
Key = 2
Output : atc toctaka ne
Decryption
Input : "atc toctaka ne"
Key = 2
Output : attack at once
Encryption
In a transposition cipher, the order of the alphabets is re-arranged to obtain the cipher-text.
For example, if the message is “GeeksforGeeks” and the number of rails = 3 then cipher is prepared as:
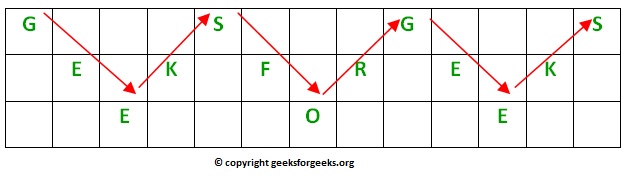
Decryption
As we’ve seen earlier, the number of columns in rail fence cipher remains equal to the length of plain-text message. And the key corresponds to the number of rails.
Implementation:
Let cipher-text = “GsGsekfrek eoe” , and Key = 3
Hence original matrix will be of 3*13 , now marking places with text as ‘*’ we get
* _ _ _ * _ _ _ * _ _ _ *
_ * _ * _ * _ * _ * _ *
_ _ * _ _ _ * _ _ _ * _
Plaintext:
Key:
Ciphered Text:
Ciphered Text:
Key:
Plain Text: