Playfair Cipher

Introduction
The Playfair cipher was the first practical digraph substitution cipher. The scheme was invented in 1854 by Charles Wheatstone but was named after Lord Playfair who promoted the use of the cipher. In playfair cipher unlike traditional cipher we encrypt a pair of alphabets(digraphs) instead of a single alphabet.
It was used for tactical purposes by British forces in the Second Boer War and in World War I and for the same purpose by the Australians during World War II. This was because Playfair is reasonably fast to use and requires no special equipment.
Encryption
For the encryption process let us consider the following example:
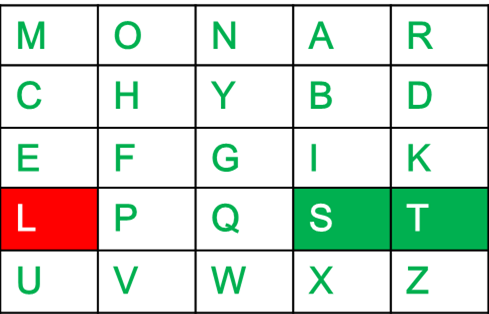
Key: monarchy
Plaintext: instruments
The Playfair Cipher Encryption Algorithm:
The Algorithm consists of 2 steps:
For example:
Plain Text: "instruments"
After Split:'in' 'st' 'ru' 'me' 'nt' 'sz'
1. Pair cannot be made with same letter. Break the letter in single and add a bogus letter to the previous letter.
Plain Text: “hello”
After Split: ‘he’ ‘lx’ ‘lo’
Here ‘x’ is the bogus letter.
2. If the letter is standing alone in the process of pairing, then add an extra bogus letter with the
alone letter
Plain Text: “helloe”
After Split: ‘he’ ‘lx’ ‘lo’ ‘ez’
Here ‘z’ is the bogus letter.
Rules for Encryption:
For example:
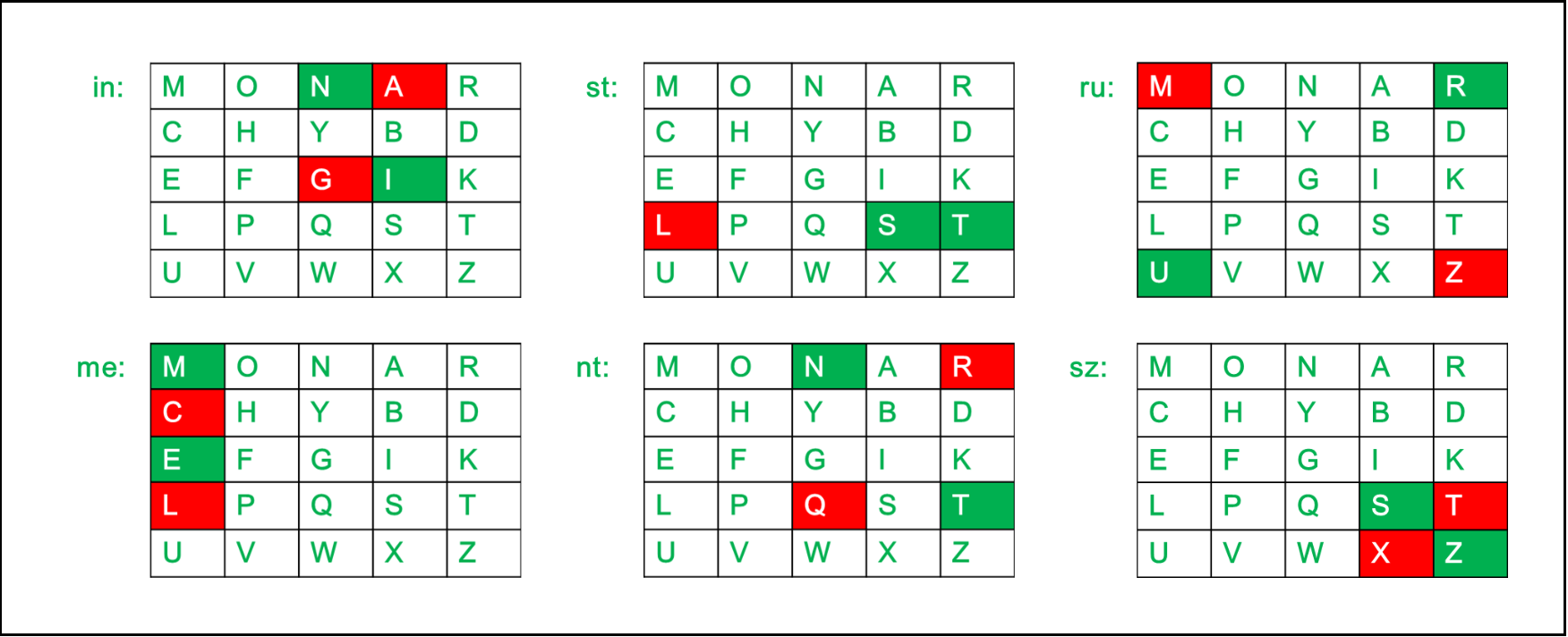
Diagraph: "me"
Encrypted Text: cl
Encryption:
m -> c
e -> l

For example:
Diagraph: "st"
Encrypted Text: tl
Encryption:
s -> t
t -> l
For example:
Diagraph: "nt"
Encrypted Text: rq
Encryption:
n -> r
t -> q

For example:
Plain Text: "instrumentsz"
Encrypted Text: gatlmzclrqtx
Encryption:
i -> g
n -> a
s -> t
t -> l
r -> m
u -> z
m -> c
e -> l
n -> r
t -> q
s -> t
z -> x
Decryption
Decrypting the Playfair cipher is as simple as doing the same process in reverse.
The receiver has the same key and can create the same key table, and then decrypt
any messages made using that key.
Key: monarchy
Plaintext: gatlmzclrqtx
The Playfair Cipher Decryption Algorithm:
The Algorithm consists of 2 steps:
For example:
Cipher Text: "gatlmzclrqtx"
After Split:'ga' 'tl' 'mz' 'cl' 'rq' 'tx'
For example:
Diagraph: "cl"
Decrypted Text: me
Decryption:
c -> m
l -> e

For example:
Diagraph: "tl"
Decrypted Text: st
Decryption:
t -> s
l -> t

For example:
Diagraph: "rq"
Decrypted Text: nt
Decryption:
r -> n
q -> t

For example:
Plain Text: "gatlmzclrqtx"
Decrypted Text: instrumentsz
Decryption:
(red)-> (green)
ga -> in
tl -> st
mz -> ru
cl -> me
rq -> nt
tx -> sz

Plaintext:
Key:
Ciphered Text:
Ciphered Text:
Key:
Plain Text: